Clone phishing: What it is and how to prevent it
Clone phishing is a technique that scammers use to steal your information. Our guide describes how it works, gives examples, and teaches you how to prevent it. Sign up for Norton 360™ with LifeLock™ Select to help protect against phishing scams, malware, and identity theft.

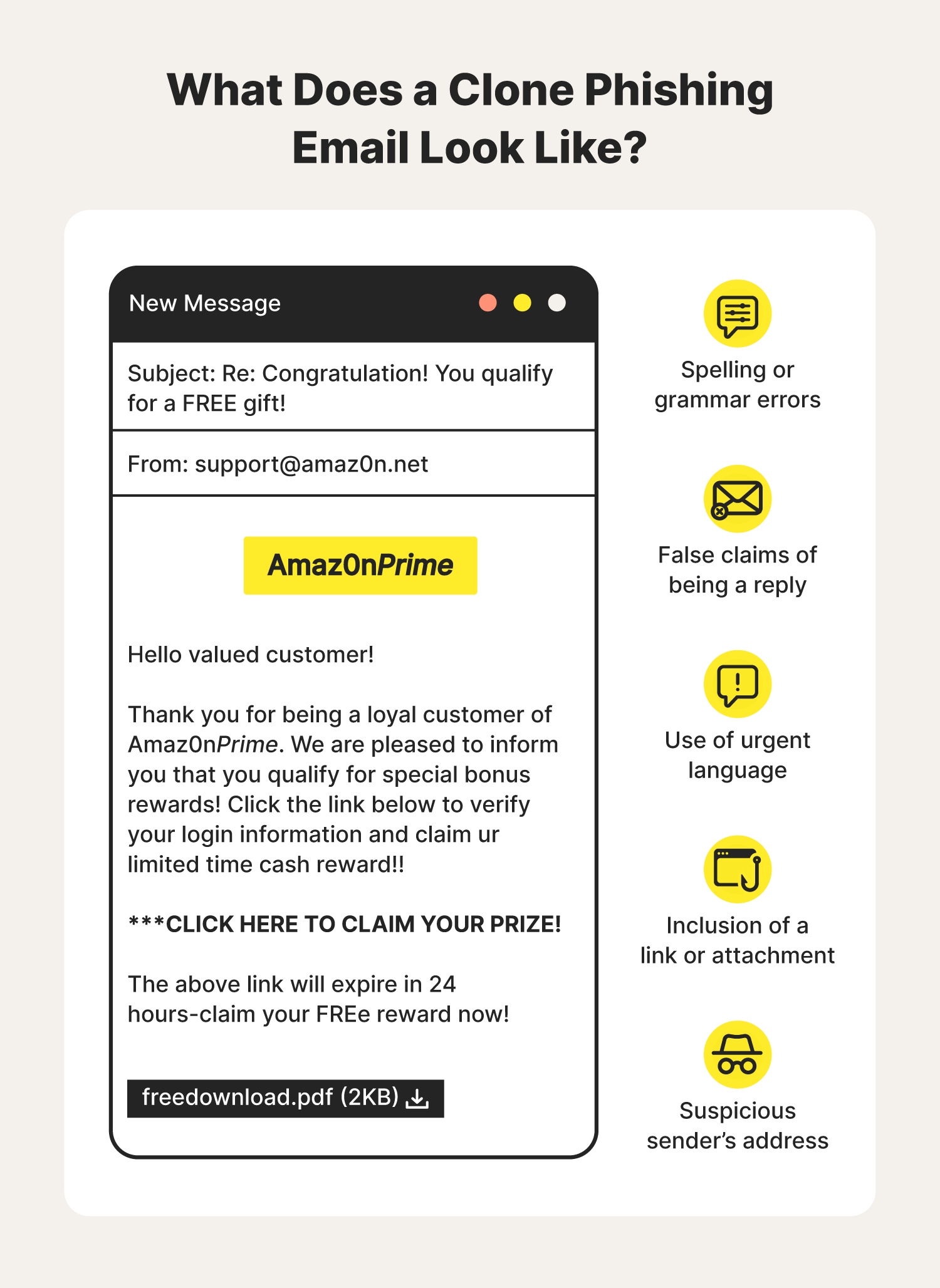
Have you ever received a new email from a brand that you love and trust, but something feels off about the message? The first couple of red flags you might notice are several typos and an aggressive tone urging you to click a link that will expire shortly. Upon closer inspection, you see that the sender's address is different, and the link sends you to an unsecured domain.
It turns out that over 75% of online scams start with an email just like this. When scammers pretend to be a trusted brand to steal information from you, it’s called clone phishing. These scam messages are loaded with malicious links and attachments that threaten your cybersecurity.
What is clone phishing?
Clone phishing is an email-based threat in which attackers create a nearly identical duplicate of a genuine email from a trusted organization. These “clone” emails contain attachments that appear similar to the originals; the difference is that they contain malware capable of stealing sensitive user information, such as usernames and passwords.
It’s important to watch out for common clone phishing scam elements like limited-time offers and claims of being an updated message. Unless you have receipts or documentation of a past conversation with the sender, the message might contain links to malicious websites and attachments loaded with ransomware.
Typically, phishing attacks prey on users who frequently bank online or shop at online marketplaces, like Amazon, where scams can take place. Be mindful of what branded emails typically look like from the online retailers you interact with most.
If a few design details are slightly off or the sender’s address is spelled differently, the message might be a clone containing potentially harmful links and files.
Clone phishing vs. spear phishing: What’s the difference?
The primary difference between clone phishing and spear phishing lies in who the cybercriminal targets and the scale of their attack. Clone phishing involves a scammer adopting a person or brand’s identity to deceive a broad range of targets using replicated websites and communication channels. In spear phishing, they use hyper-specific messages to target individuals in hopes of tricking them into revealing sensitive information.
Clone phishers aim to create believable messages from brands and people you know. Phishers replace safe links and attachments from emails that look real with malware and fake domains designed to steal your credentials. For example, a clone phishing scam might include red flags like:
- Suspicious links and attachments
- Messages with an unnecessary sense of urgency
- An unofficial email addresses
- Generic greetings
- Requests for personal information
Spear phishing scams, however, send targeted messages to a single person or organization. A spear phishing message might:
- Address you personally
- Reference a coworker
- Allude to a new payment
- Write with a casual tone
- Mention your business name
Clone phishing and spear phishing can be tough to detect. Knowing how these scams operate can help enhance your cybersecurity. Let’s look at how these types of phishing attacks work.
How clone phishing works
Cybercriminals have many methods for extracting sensitive information from everyday internet users. Here’s how clone phishing works:
- Scammers impersonate a well-known company: They create a similar web address by typosquatting and can even create a fake website. The website tries to build trust with users and make them feel like they’re in a familiar digital environment.
- The scammer sends a fake email to a large email list impersonating the brand: The message doesn’t address you personally, and cybercriminals aim to get as many people to open it as possible.
- Unsuspecting recipients open the email and follow the instructions: These users assume the message is from a trusted brand they interact with frequently. They follow a link to a fake website or are encouraged to download a malicious attachment.
- The recipient is prompted to log in to their account after opening the link: This releases their information to the scammer. The fake website will be under an unsecured domain lacking an “HTTPS” prefix.
- The scammer steals the recipient’s private information: The scammers can now log in to any account with the same login credentials. Now, users must quickly change their passwords and report the security breach.
Sketchy websites and suspicious links aren’t the only signs of a clone phishing scam. With a trained eye, there are several ways to detect fraudulent behavior.
Signs of clone phishing
Clever clone phishers make it almost impossible to sniff out their scams by accurately replicating legitimate websites or emails and exploiting their target’s trust. Here are a few clone phishing red flags to be aware of, found below.
Spelling and grammatical errors
Popular brands employ teams of experienced writers and editors to make sure their communications are as close to perfect as possible. Scammers, however, might be working with limited resources or have a language barrier, resulting in glaring errors and email typos.
Different domain extensions
Always verify that the domain extension for the link you received matches the brand’s website. For instance, if the brand you know is associated with a “.com” web address, you should be skeptical of links with domain extensions like “.net” or “.io” because the mismatch could indicate a scam.
Password managers don’t work
You already know that password managers can help secure your passwords for several different sites. But did you know they can also help you detect clone phishing attempts? If you click on a link inside a scam message and your password manager doesn’t populate your logins, it could mean that you aren’t on the normal login page.
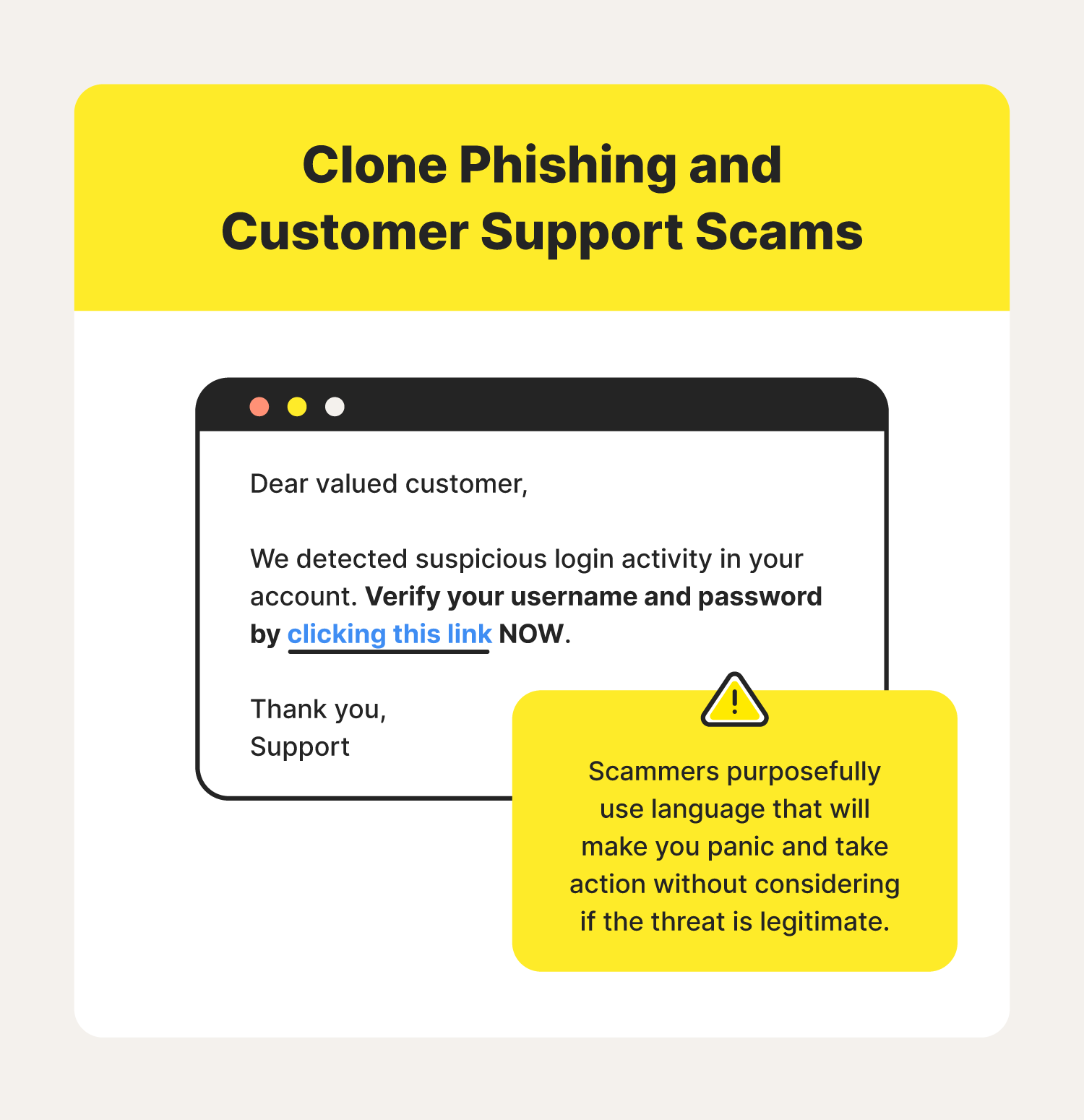
Urgent language
Rushing you is one of the ways that scammers hope to pry personal information out of you. Don’t let urgency make you forgo out of your normal safety practices.
Requests for personal information
Make sure all requests for personal information lead you to a secure domain with an “HTTPS'' prefix and that two-factor authentication is working. If these elements aren’t present, it is most likely a cyberattack.
Low-quality images and design
Blurry or pixelated logos, images, and layouts that don’t look professional are red flags. Compare suspicious emails with others from the same company.
Becoming familiar with these warning signs can help you see through convincing lies. There are a few different scenarios that scammers tend to gravitate toward. All of them, however, are intended to panic you into making a rash decision.
Clone phishing examples
There are many clone phishing templates that scammers utilize to gain sensitive information. The scams mimic a brand’s tone to convince recipients they are trustworthy representatives. Scammers study the messages trusted brands send customers when there is a security breach or urgent update.
Below are some of the most common clone phishing examples to watch out for.
1. Customer support scams
Scammers send a fake email from one of their registered social media accounts. The message will urge recipients to log into their accounts to verify user activity.
For example, you receive an email from Instagram support alerting you that your account is in danger. It asks you to log in to secure your account by clicking the provided link. Users might feel like their account information is vulnerable, so they quickly click the link that, ultimately, steals their username and password.
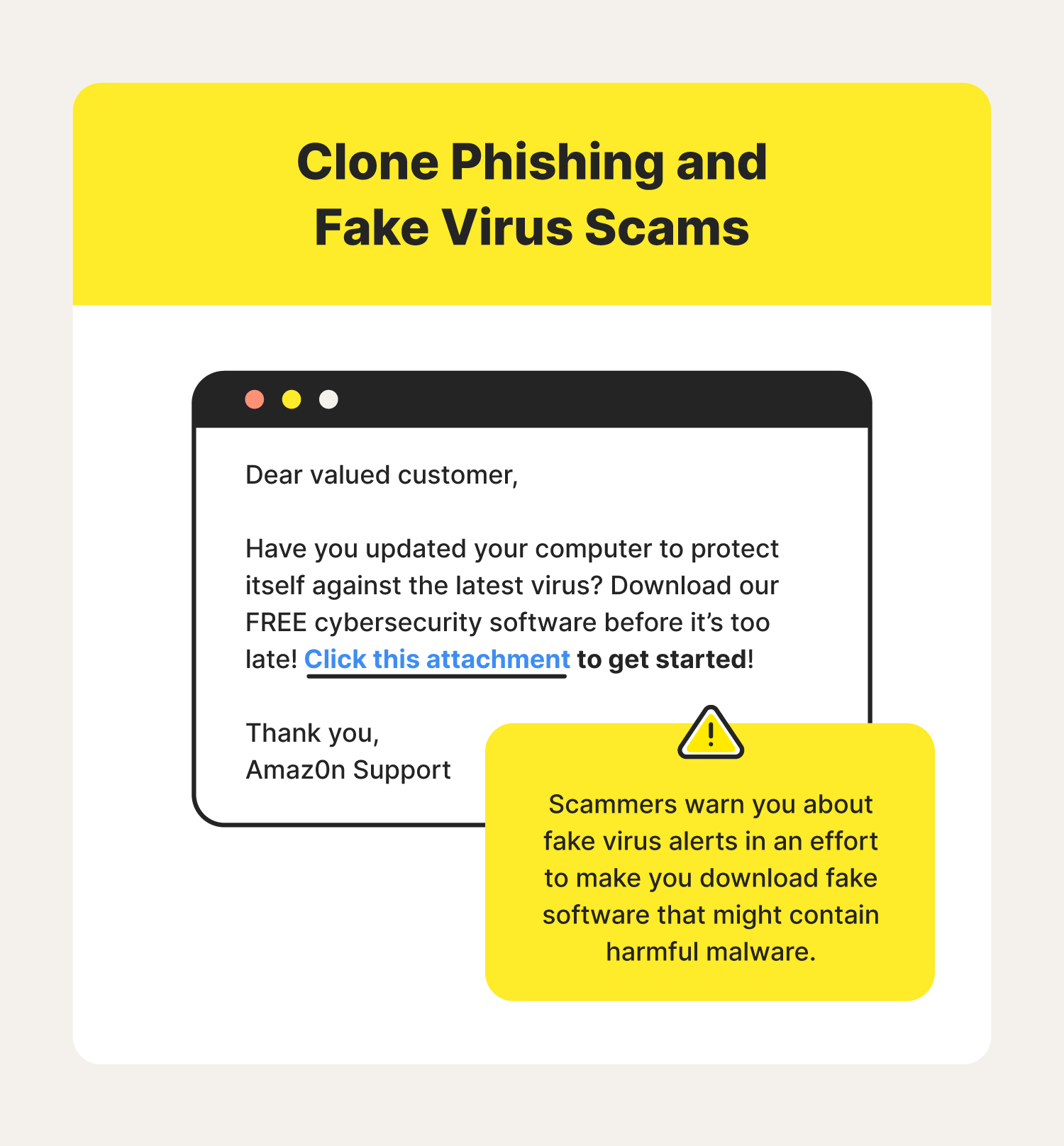
2. Fake virus scams
Fake virus alerts are often used in clone phishing scams because they make recipients think that their entire computer is at risk of being attacked (as opposed to a single shopping or social media account). Scammers also take advantage of the fact that most email platforms make it easy to download attachments without previewing their content.

86% of people say they may have experienced a phishing incident.
Meet Norton AntiVirus Basic. It does more than seek out and destroy viruses: It warns you of identity-stealing sites, safeguards your online transactions, and catches bogus email links.
Be prepared for tomorrow’s threats.
In this example, you receive an email from Microsoft or Apple alerting you of a virus on your device. The message instructs you to click a link to download an antivirus program, supposedly to prevent malware from damaging your device or stealing your identity. Unbeknownst to you, this fake virus warning is malware that can comb your hard drive for sensitive information.
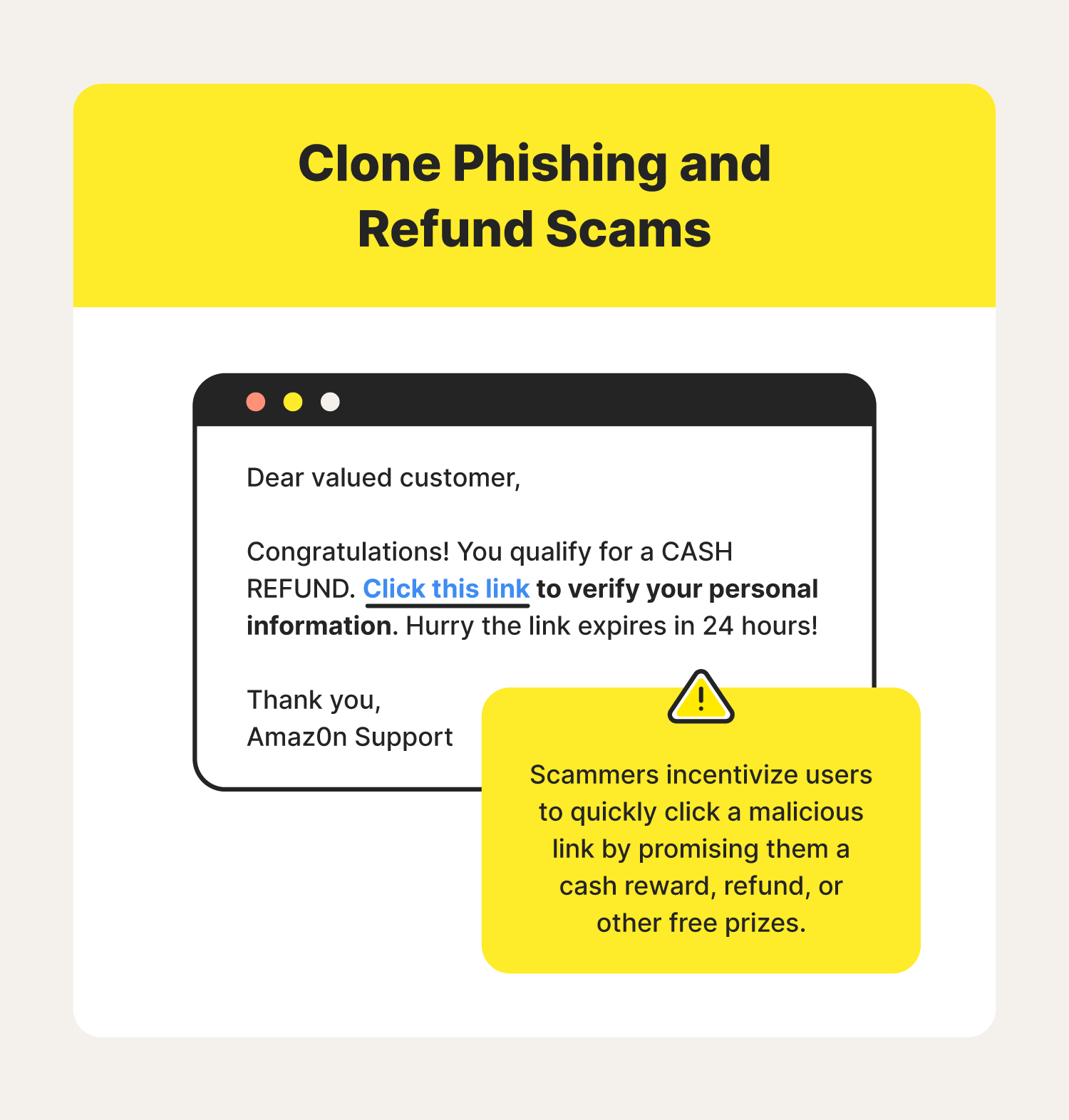
3. Refund scams
Refund scams prey on registered users of popular digital marketplaces by replicating the writing style of a brand and composing a nearly believable message about an eligible refund.
In this scenario, you receive an email from an online store, airline, or tax service saying you are eligible for a refund or free gift card. However, you must submit personal or banking information to get your reward. Cybercriminals will then use your banking information to steal funds from your accounts.
How to prevent clone phishing: 9 cybersecurity tips
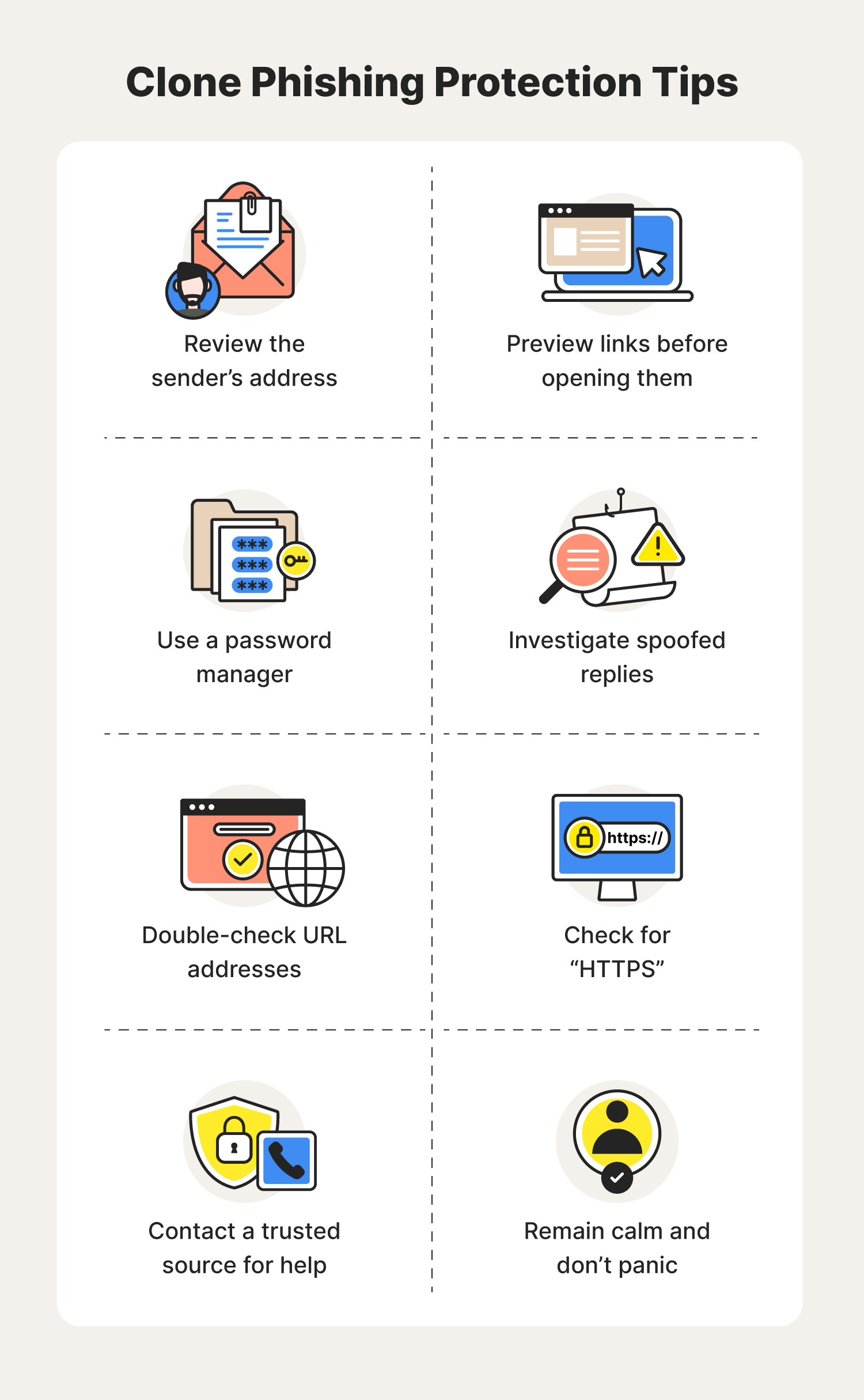
Although clone phishing can be difficult to detect, these cybersecurity tips below can help keep your personal information protected from hackers and scammers:
1. Review the sender’s address
Illegitimate email addresses might appear identical to official ones. Take a closer look, and you might notice that a few characters differ from the official address.
2. Preview links before opening them
Most internet browsers allow you to preview a link by hovering over it. If the preview looks suspicious, do not open it and report the sender.
3. Use a password manager
Password managers can help you detect replicated websites. If your manager does not auto-fill your login like it usually would, then you might be entering your information into a fake website.
4. Investigate spoofed replies
A scammer formats their message to look like a reply from an earlier conversation. But if you pay attention to this spoofed email, you’ll notice that there was never an original thread between you and the scammer.
5. Double-check URL addresses
If you already clicked a suspicious link, double-check the URL address of the “company’s” website. Does it look different from the official domain address? If so, it might be a scam. Report websites for scamming to your email provider, government agencies, and tech companies like Google and Microsoft to protect yourself and others from scammers.
6. Check for HTTPS
Secure URL addresses are normally preceded by the “https://” prefix that indicates you are interacting with a secured connection. If the SSL certificate is not there, your sensitive information could be at risk.
7. Contact a trusted source for help
If you receive a suspicious message from a trusted brand, contact their official customer support line to verify the email.
8. Remain calm
Most clone phishing scams involve a sense of urgency and targeted rhetoric that makes you panic and irrationally click on a link or download a questionable attachment. Stay calm and verify time-sensitive messages before handing over your sensitive information.
9. Use spam filters and scan attachments
Most email providers have robust spam filters designed to stop phishing emails from ever reaching your inbox. Use security software like Norton Antivirus Plus to scan attachments before downloading or opening them.
Regularly checking your email accounts is one of the easiest ways to avoid a clone phishing scam. Get familiar with how businesses normally communicate with you. It will help you spot the subtle differences of a scam.
If you believe you’ve been targeted by an email phishing scam and use the same login information as your bank account, immediately change your passwords and alert your credit card provider as soon as possible.
Protect yourself from phishing scams
Cybercriminals are constantly devising new ways to steal your data. With clone phishing, hackers exploit the trust known brands have built to trick you into voluntarily revealing sensitive information. But that’s just one of many deceptive tactics they use.
For an added layer of security online, sign up for Norton 360 with LifeLock Select. This identity theft protection service grants you access to features like malware detection, phishing warnings, and information-exposure alerts. Together, these can help keep you informed about the security of your personal info, enabling you to take fast action and minimize potential damages.
FAQs about clone phishing
Have more questions about clone phishing? We have answers.
How do scammers clone emails?
Scammers will look at emails from brands and copy the structure and layout of those emails to create passable fakes. Unsophisticated scammers might create copies that don’t use the proper branding and formatting. If you see a message that looks old or poorly designed, it could be a scam.
What is spoof phishing?
Spoof phishing is when a hacker creates phishing messages specifically for you based on public information. This type of phishing can include using data they find on your social media profiles; people search sites, and other details they find on the dark web. These messages can be very convincing, so you must look for email addresses and URLs that don’t align with the brands or people the spammer is spoofing.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips and updates.